What is Kerberos?
The protocol derives its name from the three-headed dog Kerberos from Greek myths.
Initially, it is developed by MIT (Massachusetts Institute of Technology) and a version of Kerberos is rolled out by Microsoft in Windows 2000.
Kerberos is a computer network authentication protocol. It verifies every user who wants access to any server. Kerberos only allows those users that are authorized or that have permission to connect with a server.
It uses symmetric-key cryptography that helps to secure data more efficiently. Now let’s understand the meaning of symmetric-key cryptography. In symmetric-key cryptography, a private key is used for both the encryption and decryption of data. It simply means you need a private key to encrypt data and decrypt as well.
The three heads of Kerberos represent the Client, the Server, and the Key Distribution Center (KDC). The client and the server are general terms but KDC is one that provides a ticket to the authorized user. Basically, it contains two main things, Authentication Server and Ticket Granting Server.
Main Components of Kerberos
There are some essential components of Kerberos, that all are needed to complete a smooth flow of the Kerberos cycle.
- Client: The client is one who initiates communication for a service request.
- Server: It contains the service that the user wants to access.
- Key Distribution Center: The KDC divide into basic three parts i.e., the Database (DB), the Authentication Server (AS), and the Ticket Granting Server (TGS).
- Authentication Server: It verifies the user’s details, if the authentication happens successfully then it generates TGT (Ticket Granting Ticket) that provides a time span for a limited time or fixed time.
- Ticket Granting Server: TGS issues a service ticket as a service that verifies a user to the server and grants access to the user.
Detailed Structure of Kerberos
Here is the detailed structure of Kerberos, now you can also easily define the structure.
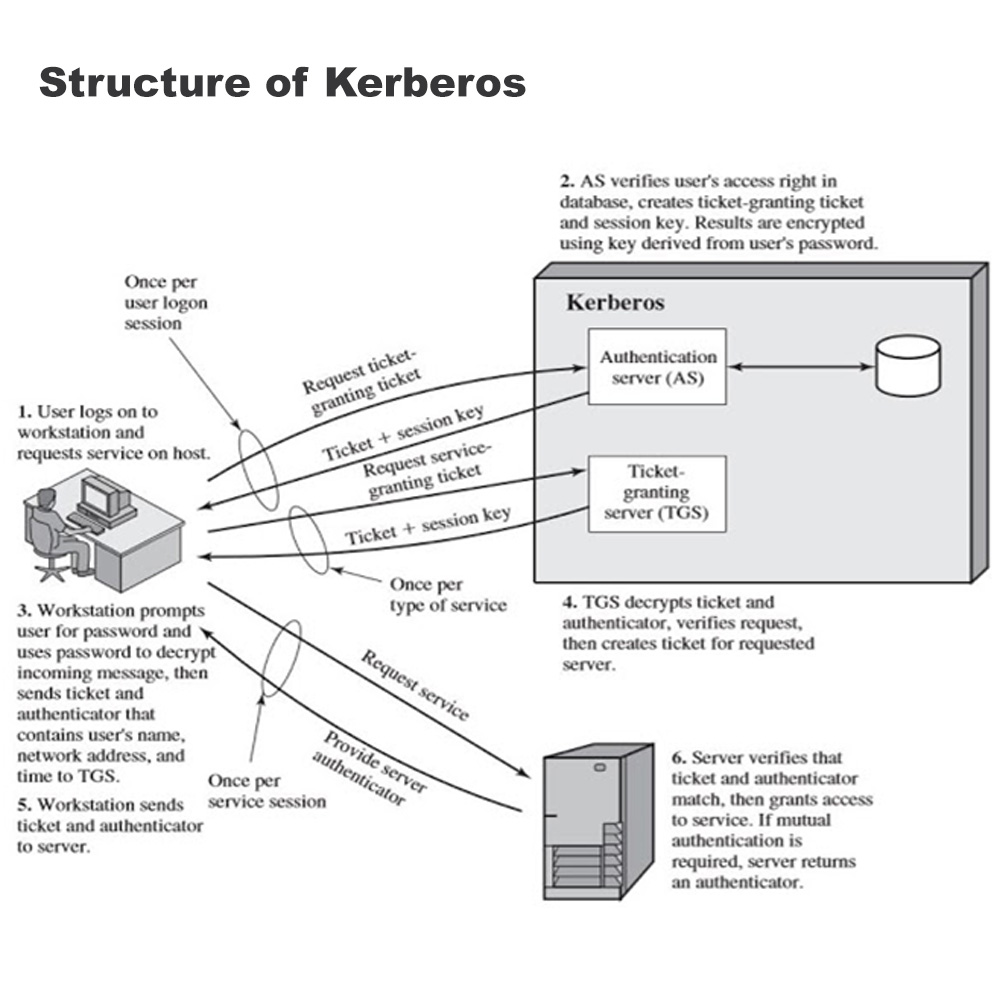
There are 3 main things i.e.,
- The User (it can be a client or employee of an organization)
- KDC (Key Distribution Center)
- Server
Let’s understand it step by step
- First of all, the user needs to be verified by the KDC who wants access to the resources that are hosted by the server.
- After verification, the user requests a ticket from KDC and here Authentication Server verifies the user’s details.
- If the authentication happened successfully then AS provides a Ticket Granting Ticket that ensures a time span. It simply means that it provides a ticket that ensures a fixed amount of time for the user to be connected to the server.
- Now a user can access the resources that are available on the server for a time of span.
Conclusion
In the technological world, cybercrime is an unfortunate fact. So we need to secure our data from unauthorized users who want access illegally.
There are many technologies that provide highly secured functions to protect our data.
One of them is Kerberos that uses secure-key cryptography to secure our data. Basically, it first verifies the user’s detail, if the users verified successfully then it provides a ticket and then Ticket Granting Server (TGT) issue a service ticket.
And at last, the server verifies the details and provides access to the host of the resource by it.






